Setup and use of BurpSuite
1.BurpSuite installation and configuration
BurpSuite function introduction
BurpSuite is an integrated platform for attacking web applications and contains many tools. BurpSuite has designed many interfaces for these tools to speed up the process of attacking applications. All tools share one request, and can handle corresponding HTTP messages, persistence, authentication, proxy, log, and alert.
Burpsuite is written by JAVA language, so Burpsuite is a cross-platform software. But unlike other automated testing tools, Buripsuite does not require any input to complete the test during the testing process, but requires manual configuration of certain parameters to trigger the corresponding behavior to complete the test.
2.BurpSuite Proxy Module
Burp Proxy is the core of Burp Suite’s user-driven testing process function. Through the proxy mode, we can intercept, view, and modify all data transmitted between the client and the server.
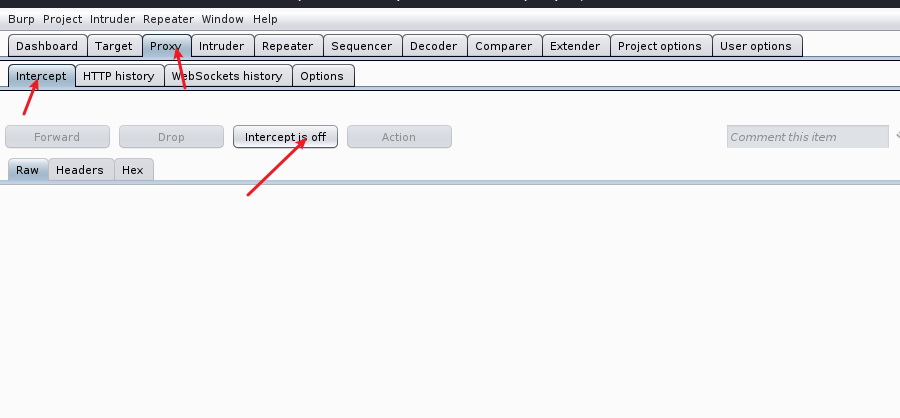
1.Intercept
Forward means sending the truncated HTTP or HTTPS request to the server.
Drop means to discard the truncated HTTP or HTTPS request.
Intercept is on and Intercept is off indicate that the proxy truncation function is turned on or off.
Action means sending the HT TP or HT TPS request truncated by the agent to other modules or doing other processing.
Switch the Raw Hex Params Header to Intercept to view different data formats.
2.HTTP history
HTTP history is used to view submitted HTTP requests.
Fiter can filter and display certain HTTP requests. Click Filter to open it. For the specified URL, you can right-click and perform other operations. WebSockets history is similar to HTTP history.
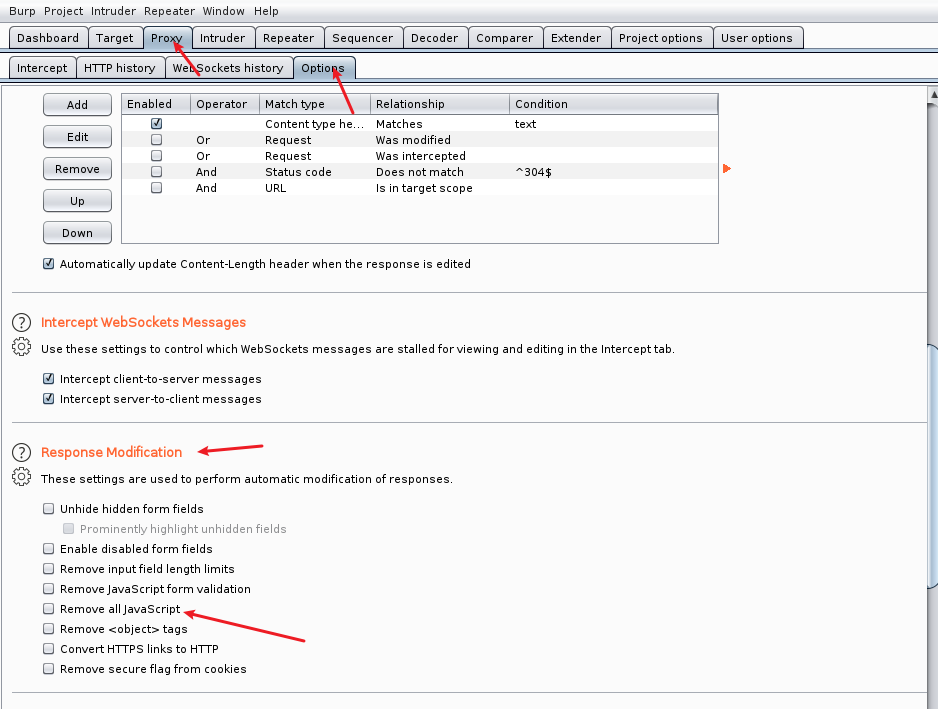
3.options
Options have functions: proxy monitoring settings, poke client requests, truncated server responses, truncated WebSocket communications, server-side response modification (bypassing JS verification file upload), matching and replacing the content in the HTTP message, connecting to the Web server through SSL Configuration, other configuration options.
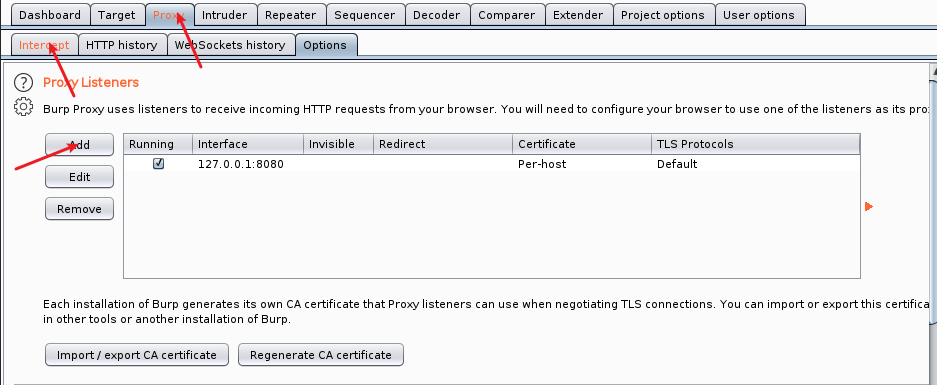
4. Set proxy listener
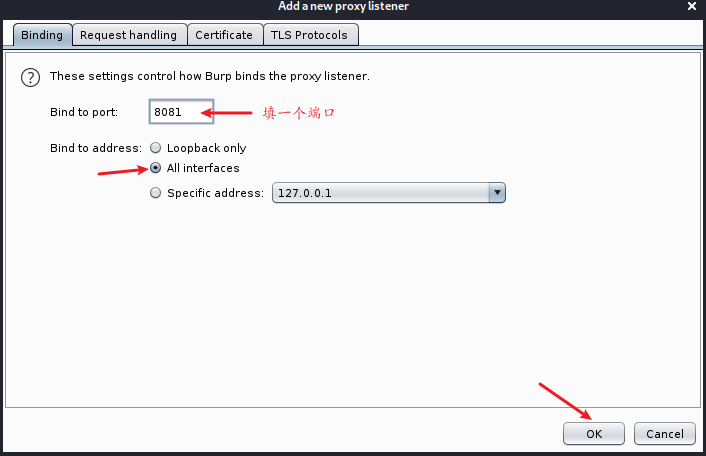
Cut off data traffic by setting Proxy Listeners. For example, setting the listening port and so on. BurpSuite listens on port 8080 by default.
Modify the port:
- Turn off truncation
2.options->edit
Modify the port, click running
Modify the browser port
Internet Options -> Connection -> LAN Settings
Modify the port
5. Set intercept client requests
By setting Intercept Client Requests to intercept qualified HTTP requests.
6. Set Intercept Server Response
Filter out eligible HTTP responses by setting Intercept Server Response.
7. Set to truncate Websocket communication and modify the content of Response
8. Match and modify HTTP messages
You can modify the content in the HTTP request and HTTP response.
3.Burpsuite captures mobile APP traffic
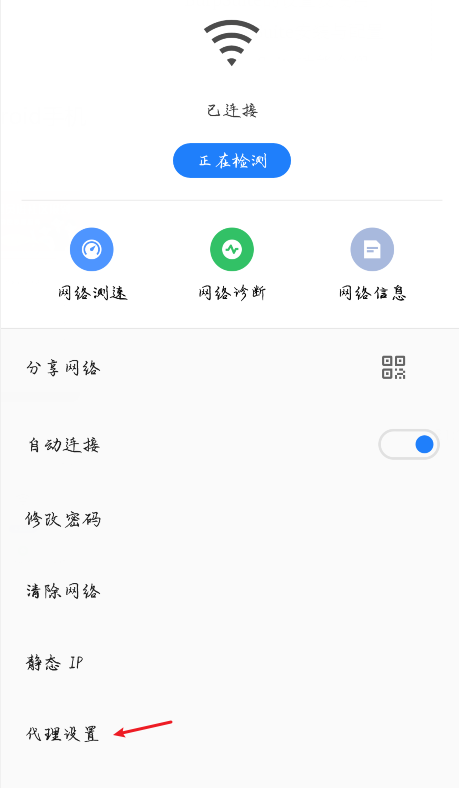
At present, the communication of WebApp (mobile phone App) still uses the HTTP protocol for corresponding communication. You can set the proxy through Burp, and then set the network proxy on the phone, and intercept the mobile APP traffic through Burp.
- Burpsuite is set to cut off the traffic of all network cards, then all the hosts in the office city network can access the network through the proxy.
Check the computer ip
In the mobile phone network settings, fill in the corresponding agent.
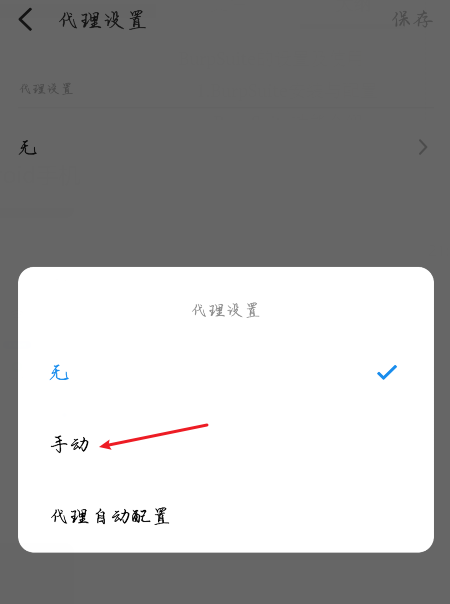
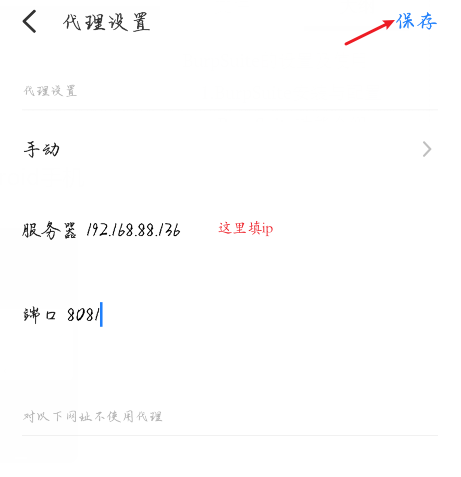
- Burpsuite turns on truncation
4.Burpsuite removes JS scripts (bypassing JS file upload verification)
JavaScript—-a literal scripting language. It is a dynamically typed, weakly typed, prototype-based language with built-in support types. Its interpreter is called the JavaScript engine, which is a part of the browser and is widely used as a scripting language on the client side. It was first used on HTML (an application under the Standard Universal Markup Language) web page to add dynamic functions to HTML web pages. . For example: JS verification for uploaded files.
You can also use the browser audit tool to delete JS directly
5. Introduction to Burpsuite Target
The Burp Target component mainly consists of three parts: site map, target domain, and Target tool. They help penetration testers to better understand the overall status of the target application, which target domains the current work involves, and analyze possible attack surfaces.
The definition of scope in Target Scope is relatively broad. Generally speaking, when we conduct penetration testing on a product, we can restrict the interception of content by domain name or host name. Here, the domain name or host name is the scope we are talking about; if we If you want to limit it more fine-grained, for example, if you only want to intercept all requests in the login directory, we can also set it here. At this time, the scope is the directory.

